Mobile Device Management
Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers, laptops and desktop computers. Mobile device management is usually implemented with the use of a third party product that has management features for particular vendors of mobile devices.
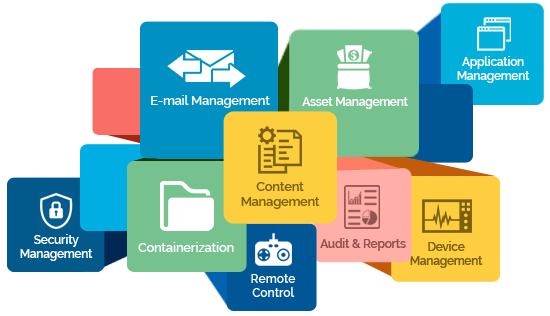
Mobile device management is typically a deployment of a combination of on-device applications and configurations, corporate policies and certificates, and backend infrastructure, for the purpose of simplifying and enhancing the IT management of end user devices. In modern corporate IT environments, the sheer number and diversity of managed devices (and user behavior) has motivated MDM solutions that allow the management of devices and users in a consistent and scalable way. The overall role of MDM is to increase device supportability, security, and corporate functionality while maintaining some user flexibility. Many organizations administer devices and applications using MDM products/services. MDM primarily deals with corporate data segregation, securing emails, securing corporate documents on devices, enforcing corporate policies, integrating and managing mobile devices including laptops and handhelds of various categories. MDM implementations may be either on-premises or cloud-based.
Mobile device management is typically a deployment of a combination of on-device applications and configurations, corporate policies and certificates, and backend infrastructure, for the purpose of simplifying and enhancing the IT management of end user devices. In modern corporate IT environments, the sheer number and diversity of managed devices (and user behavior) has motivated MDM solutions that allow the management of devices and users in a consistent and scalable way. The overall role of MDM is to increase device supportability, security, and corporate functionality while maintaining some user flexibility. Many organizations administer devices and applications using MDM products/services. MDM primarily deals with corporate data segregation, securing emails, securing corporate documents on devices, enforcing corporate policies, integrating and managing mobile devices including laptops and handhelds of various categories. MDM implementations may be either on-premises or cloud-based.
Mobile Security
Securing mobile devices has become increasingly important in recent years as the numbers of the devices in operation and the uses to which they are put have expanded dramatically. The problem is compounded within the enterprise as the ongoing trend toward IT consumerization is resulting in more and more employee-owned devices connecting to the corporate network.
Microsoft Intune
Microsoft Intune is a cloud-based service in the enterprise mobility management (EMM) space that helps enable your workforce to be productive while keeping your corporate data protected. Similar to other Azure services, Microsoft Intune is available in the Azure portal. With Intune, you can:
- Manage the mobile devices and PCs your workforce uses to access company data.
- Manage the mobile apps your workforce uses.
- Protect your company information by helping to control the way your workforce accesses and shares it. Ensure devices and apps are compliant with company security requirements.
